Before & after the cybersecurity training
Let’s pose a scenario: Your top client receives an email from you that sounds awfully suspicious, it may go like, “Hey, I sent you the document you requested. Click this link to download the PDF.” If your clients are smart, they would quickly reply to you if they think something is strange about the email. They would want to confirm if you actually sent the email. Imagine what would happen if your mailbox was either spoofed or compromised.
Attackers sent these emails to all of your clients in an attempt to either infect their computers with malware, and/or to steal their credentials.
What if the attackers succeeded? What would that do to the image of your company?
How would that change the dynamic of your client relationship?
Sure, we can implement tools and security measures, but socially engineered attacks are so good and they may still be affective. It is that reason it’s still the top tool used by cyber criminals.
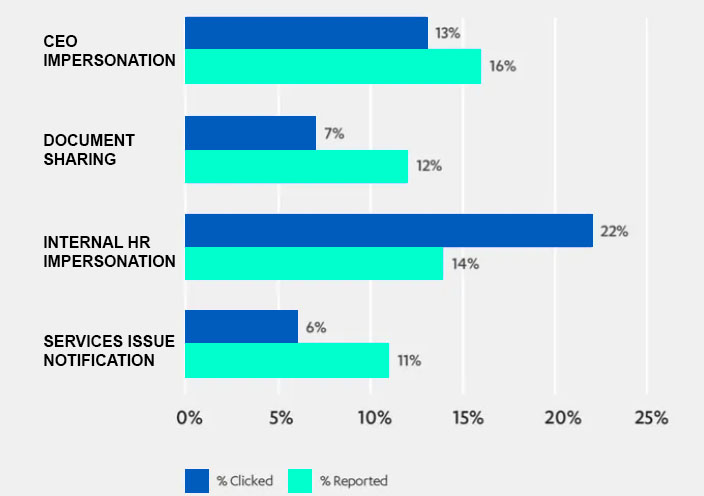
F-Secure represents the percentage of people clicking and the percentage reporting of a phishing simulation.
F-Secure collaborated with four multinational businesses to conduct campaigns utilizing one of four distinct phishing emails: a purported message from human resources, a fake CEO fraud notice, a forged document-sharing notice, and a bogus service notification. In average, 12% of users clicked on the phishing email in their inboxes, but the rate varied significantly.
The median time to report a suspected phishing attack was 30 minutes, which is reasonable yet problematic since 25 percent of those who responded to a phishing email did so in the first five minutes, according to Matthew Connor, F-Secure’s study.
What does cybersecurity training look like?
Many businesses, both large and small, have prioritized cybersecurity education or Security Awareness Training as a strategy to raise awareness about current and developing cybersecurity threats. Awareness training is a form of education that aims to educate consumers and workers about their role in preventing information security breaches.
Cyber hygiene education, for example, helps employees recognize potential cyber assaults via email and the internet by instructing them on how to avoid being affected by malware or phishing scams.
The training is normally conducted in a form of videos and slides, the effective training engages the student by showing them the possibilities of what a phishing attacks looks like. It’s important to use training that focuses on details such as making sure the logos are correct, verifying for typos, and looking at proper signatures.
Cyber training is more than just e-learning, it’s also about building awareness of your personal information security practices, whether it’s using the internet safely or taking precautions against ransomware attacks.
So, how effective is it?
Use of the content of phishing simulations was found to be more effective for cybersecurity training than simply using examples or abstract explanations. Studies have shown that real world scenarios are highly impactful in changing awareness and helping companies improve their security posture against these attacks. On average, people would report a suspicious email within 30 minutes of receiving it.
So how do you measure the effectiveness?
In order to measure the impact of a phishing simulation, one must determine what percentage of employees will click on the suspicious email without training, and then compare this against your company’s actual results. In addition to 4 distinct types of attacks in F-Secure’s study, there are other approaches to simulations. Some companies will design phishing emails that aim to mimic the company’s own communication style. This allows for employees to experience what it feels like to click on a legitimate-looking email from their manager or colleague.
People are much more likely to respond if you ask them in person rather than sending them an email, so taking this approach can increase participation in the training.
How do you measure security postures?
The client teams were evaluated based on their post-test results and how they responded to the phishing simulation. There are many variables when it comes to measuring your company’s security posture, including the percentage of employees who received and reported the email, as well as how quickly they responded to the phishing simulation.
The study found that those who had not been trained were 97 percent more likely to click on one of the malicious links than those who had completed training.
Cybersecurity Education gives employees knowledge about how to protect themselves and their company, allowing them to be more aware of threats and be better equipped to report any suspicious activity. This training is especially vital when it comes to showing your clients that you take security very seriously.
Depending on the industry, working with clients such as financial institutions, or clients in highly regulated industries such as healthcare, knowing that you have taken all the appropriate steps in order to train your employees to help safeguard your clients’ data/network can go a long way in securing long-term working relationships.
Training followed up by testing is one of the best indicators of how effective the training was. If your business needs help developing a security training strategy, if you want to test and see how aware your employees are in regards to cybersecurity reach out to AlphaCIS. We can do live seminars for security training and help develop a strategy that fits your business needs. Reach out to us at 678-619-1218

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



