What it was like for a CPA firm to survive a cyberattack
I met Joe at a networking event, he is a CPA and owns his own Public Accounting Firm. Over time we became friends and I assisted his MSP (Managed Services Provider) on several IT projects.
He employs 12-15 accountants depending on the time of the year. One Friday, Joe noticed that his systems were running a little slow. Being that it was a Friday afternoon, and having had dinner plans in a few hours with his family and a few friends, he chalked it up to system updates, slow internet, or maybe just him being impatient because it’s the end of the week!
He quickly finished what he was doing, packed up his things and headed home to get ready for dinner. He forgot about work for the rest of the weekend.
Let’s fast-forward to Sunday… Joe gets a frantic text in all caps from a remote employee, Amber, that said, “I logged into the computer and wasn’t able to open any company files. The error says, “Unknown File Type,” on any program or document I click.” She looked further and noticed that the only text document that she was able to open was labeled “HELP_Instructions”.
When she opened the document it read the following:
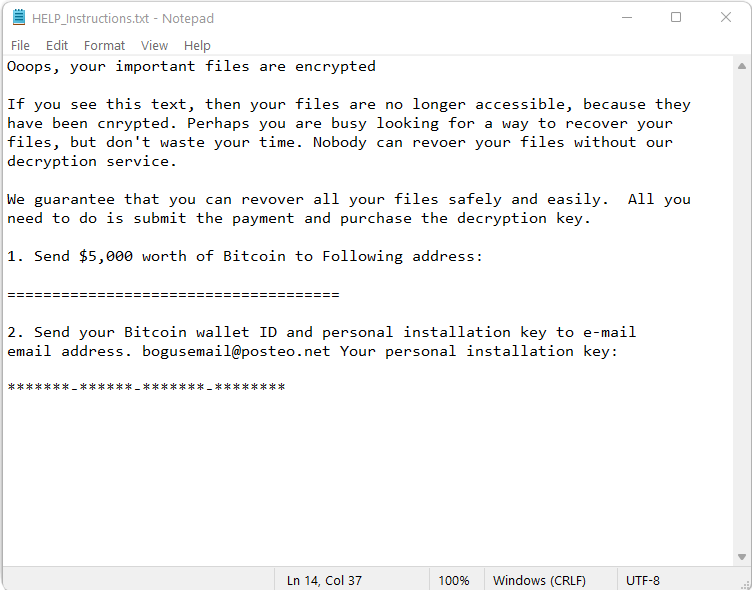
OOPS! Looks like all of your files have been encrypted.
Decrypting your files is only possible with the following steps:
(Listed an email address and a link to a bitcoin wallet requesting somewhere in the neighborhood of $5,000 to decrypt the system.)
Amber quickly takes a picture of her screen and texts it to Joe.

Joe meanwhile is enjoying a nice sunny day at the park, watching his son’s soccer practice. Joe looks down at his phone and sees the fuzzy image of the screen shot with an ALL CAPS message from Amber panicking.
Joe quickly tells his wife he has to run into the office. Joe’s stress level is off the charts as he rushes into his office to see what is going on for himself.
He sits in front of the computer he left just a day and half ago and tries to login with his usual network credentials, but to his surprise he is greeted with several error messages stating that his “account was not found”, “domain trust lost,” and several others. Franticly he is finally able to login using the computer’s local account.
First things he does is opens Ultra Tax (their primary software that runs from a database on the server) and sees a message “database not found” error. He then briskly walks to the data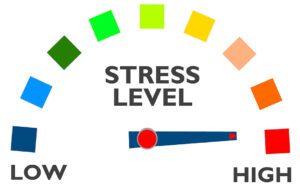 cabinet and checks that the server is powered on. All the lights are flashing so he heads back to his desk and tries connecting to his mapped network drive where ALL of his company files and client data reside.
cabinet and checks that the server is powered on. All the lights are flashing so he heads back to his desk and tries connecting to his mapped network drive where ALL of his company files and client data reside.
To his horror he finds every.doc, .pdf and .jpg file has an additional file extension attached to it with an unknown icon showing up for each one. No matter what file he clicks nothing opens while the error messages continue to pop up on his computer with the same document instructions he was texted earlier by Amber.
Upon further inspection he finds the same text document in every folder of his server and on his local computer that has the same ransom note with instructions on how to unlock his files and where to send bitcoins.
Joe freaks out but quickly remembers he has a Network Attached Storage (NAS) backup that he is fairly sure backs up all of his files daily. He is angry but breathes a sign of relief as he knows this won’t keep his systems down for long and he can have his IT support team restore from backup in no time.
He quickly logs into his NAS and is instantly greeted with the familiar HELP document and file extensions on every single backup file on his NAS.
Joe gets a knot in his throat as he comes to term of what just happened to his systems and most importantly to his business. What do you do??!!
Unfortunately for Joe the hackers won this round. He contacted FBI but had no other choice but to either close down shop and go out of business OR to pay the $5,000 to the cybercriminals in hope he would get the email response back with a decryption instructions.
After registering an account on Coinbase he purchased the Bitcoin amount requested in the ransom note and sent it to the wallet address in the instructions.

He awaits anxiously hitting refresh on his email every few minutes in hopes to receive some word from the people who are holding his business hostage.
Several hours had passed when he received a new email notification. Attached was a small zip utility with an EXE file inside called decryptor. Joe opens the file and finds a cumbersome interface, where you could select files and click decrypt. He selects all the main files in his data folder that contains his database of TaxWorks and Office Tools and clicks decrypt.
The utility starts running and showing the log of each file that it is decrypting. The speed at which its decrypting is painfully slow and Joe spends the next 5 days periodically checking the tool as it bounces from decrypting to Not-Responding.
Joe had to call a meeting and explain to his employees what happened, and why they are getting next week off work. This whole debacle caused Joe to miss out on thousands of dollars in business as well as employee cost on top of the ransom he had to pay.
Unfortunately, Joe is not the only person that this sort of thing has happened to. Many business owners show back up to work on Monday only to discover the same thing Joe experienced. It is one of the scariest things a business owner can face. In this instance, Joe was lucky that the hackers came through on their word and gave him the key to decrypt his files. Many pay money and never see that email that Joe received.
After having an IT team dig further into it, he discovered that the breach occurred from a desktop that has been used by temp workers. The hackers gained access to the machine inside the network, where they ran several discovery tools that found other network resources, such as: the file server, Active Directory database, other machines, and the NAS. They executed the code using the same authentication they used to login to the machine. They then spread the loader on all machines and the server executing the encryption algorithm.
Luckily for Joe, he was able to resume business after decrypting his files, changing all of his passwords, removing all unused users, removing the affected computers from the network, running and updating AV on all machines, and changing all the VPN and firewall settings.
What theoretically would have happened if Joe used “Zero Trust Security,” or Beefed Up his Network Security?
Let’s assume his network would have still been compromis
ed by the machine in question. This machine’s access level would have to be verified with a 2FA before access to the network would be granted, and because the network is segmented, this machine would only have access to a few folders and databases, and would have limited timeout built in before re-authentication would be required.
The backup drive (NAS) would have been on a segregated security group and would require a different 2FA and username not linked to the Active Directory.
Odds are the computer that was infected would have the documents and systems encrypted, however it would stop there.
Due to limited access and external authentication required it would be very difficult for the malware to spread laterally across the network. The NAS would not be affected and anything lost could be easily restored without paying a ransom or waiting for days while the decryption occurs.
Here is why you should consider a Zero Trust security approach for your business.
I know some of you have heard the term, “Zero Trust,” being bounced around. If you read the technical documents, it might seem a little overwhelming with all the fancy technical jargon that goes into it. So, let’s try to explain what “Zero Trust” really is, and why it is important to start thinking about it for your business. The Federal Government just passed a bill to implement this into the government’s systems, and the private sector should also follow!
What is Zero Trust Security?
Zero Trust security means that every person and device need to be verified before they can access the private network. This assumes that no device is trusted and users must verify their credentials every time they require access to the files, with temporary timeouts built in where a user must re-authenticate.
Segmenting the network
This is part of the “Zero Trust,” where a network is broken out into security segments and users/programs only have access to small portions of the network, instead of the network as a whole.
This segmentation allows for the Admins to quarantine all accounts and devices in specific groups, if compromise on the network has been discovered, preventing other systems on the network from getting affected.
Multifactor Authentication
Multifactor Authentication, should be everything such as system logins, cloud based services, local network software, and files that need to authenticate with 2FA.
Everyone knows employees either tape their passwords to their monitors, under the keyboards, or use the same password everywhere. Something like 60+ percent of people use the same password across multiple accounts. When the website you use to purchase workout clothes has its user database breached, those usernames and passwords end up on the dark web. These databases become available to hacking groups which is then used in brute force attacks on open systems such as the one that Joe had.
What you can take away from this?
What we can learn from Joe is that being prepared for a cyberattack can go a long way in keeping your business running. You don’t have to incorporate the Zero Trust security model over night or to the full extent, however, bits and pieces can go a long way! Multifactor Authentication should be the norm on all cloud based and VPN services. Backup devices should be segregated from the rest of the network, employees should only have access to files and applications that are necessary to their job function, complex password requirements and requiring employees to change their passwords every 30 days is also crucial in maintaining the security of your systems. Bring up these concerns with your Managed Services Provider (MSP) company. If you need help or additional advice on how to improve the security of your network, reach out to AlphaCIS to get your systems secured and avoid becoming the statistic of cybercrime.

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity