How hackers are getting around Microsoft Defender
Microsoft presents Windows Defender as a one-solution fits all, however as we learned that is certainly not the case in the cybersecurity world. Cybersecurity should be tailored towards a particular business, there is rarely one size fits all approach here.
Microsoft Defender lets users add locations or network locations to the list of excluded areas to be scanned for malware/viruses.
Users commonly add folders and paths to Microsoft Defender in order to increase the speed of the application or prevent false detection in order to allow their apps to run properly. What was recently discovered, however, is that the file path of the folders to be excluded can be accessed by any local user regardless of their permission level through the registry key or command prompt.
This means that its very easy to lookup the folders that are excluded from malware detection.
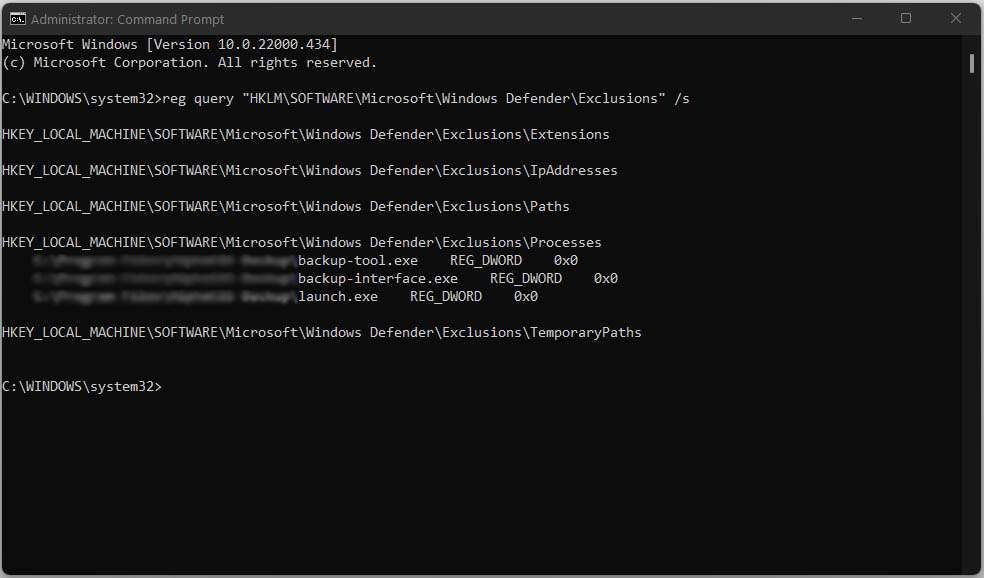
This allows the threat actors to store malware in those excluded folders. Simply by running command reg query in command prompt will give you a list of folders and files that are excluded from the scanning.
Well, you might be thinking that they still need access to the system in order to view this information. Unfortunately, many machines are compromised already and hackers are just looking for ways to move laterally across the network.
We did our own test by placing malware sample into the computer and tried to run it. Microsoft Defender instantly stopped the action and blocked and removed the files. Then we placed the malware into an excluded folder and ran it. Microsoft Defender gave no warning and allowed for the entire machine to get encrypted.
This is why we recommend our clients to upgrade to Windows 11…
This has been an outstanding issue with Microsoft Defender for quite some time now (like years!). I want to note that however when running the command in Windows 11, accesses was denied until we ran the Command prompt as Administrator. In Windows 10 this did not require higher privileges in order to run. This is why we recommend our clients to upgrade to Windows 11 due to higher security measures that Microsoft has taken.
If your business only relies on Microsoft Defender as the only barrier to stopping malware, phishing or all other cyber attacks I would urge you to have someone assess your systems. Cybersecurity is not just a matter of installing a software and being done with it.
It’s important to look at all factors of how work flow happens, what applications are used and what critical surfaces are exposed on your network. As you can see software alone is just not enough in today’s world, it has to be a combined effort with the use of limited permissions, firewall policies, cloud spam filters AND machine learning software that relies on learned user behavior in order to protect organization.
If you need help assessing your system for cybersecurity risk AlphaCIS can help. We are a Managed Services Provider (MSP) located in Metro Atlanta area specializing in cyber security. Give us a call (678) 619-1218

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



