60%
Small businesses' will close after experiencing a data breach within 6 month according to Experian.
"Most businesses, in my experience, are ill-prepared to handle a cyber attack; very few even know where their data is backed up to or if their backups are even good..."
— Jackob S, CIO Consultant
Need To Secure Your Systems?
FACTS
Antivirus alone will not keep your business safe from a cyber attack.
Most common cyber threats are socially engineered attacks such as phishing designed to steal passwords or install malware on your machine. Cyber criminals gain control of the infected machine and using windows features and legitimate programs infiltrate your network, steal data, and encrypt your systems. We put in place products, services, procedures, and strategy designed to prevent your organization falling victim the attacks such as:
PHISHING ATTACKS
Antivirus does not offer a robust cloud filter that scans emails prior to you receiving them in your mailbox. Office 365 alone does not offer an effective email spam filtering solution
ZERO-DAY MALWARE
Antivirus scans file signatures and compares them to previously known definitions of malicious code. Zero-Day is malware that does not have the definition yet and would go unnoticed by most Antivirus programs
RANSOMWARE
Ransomware could encrypt your system by using built-in Windows functionality like Bitlocker. Antivirus would not perceive this as a threat and allow the encryption to continue
BROWSER PLUGIN
Much of the malware like key loggers will get it’s way into a computer using a browser extension that if user is allowed to install would often times bypass most Antivirus solutions
ABNORMAL BEHAVIOR
Antivirus does not monitor data usage, such as what would be present if threat actors would be offloading your data to their server prior to encrypting it. (Data Breach)
OUTDATED ANTIVIRUS
Antivirus constantly updates for new threats as they emerge, so if your subscription runs out, or you ignore the update, it will render the antivirus less effective
GIVING YOU PEACE OF MIND IS WHAT WE DO!
ZERO TRUST
Limiting what the user can access and do to only the minimum permissions needed to perform their jobs. This includes not only file access but limiting what can be installed and ran on a computer
MONITORING BEHAVIOR
Once a user's typical work day is learned and set, we can use this as a baseline for the "norm." Our software then scans for or blocks activity that falls outside the "norm." All virus definitions and updates are centralized and standardized so that a user is not responsible to keep up with updates
CLOUD SERVICES PROTECTION
With cloud services becoming the new norm, keeping your cloud infrastructure protected is more important now than it has ever been. Putting in place safeguards to ensure your data, customer data, and your systems are protected is crucial to overall security of your organization. We eliminate threat vectors and reducing attack surface as part of keeping your cloud infrastructure secure.
EMAIL SPAM FILTERING
We incorporate machine learning AI cloud based spam filtering. This means in addition to your Office 365, it scrubs emails prior to delivering them to your mailbox. Greatly limiting your exposure to phishing attacks
BUSINESS CONTINUITY
Develop an action plan of how to mitigate damages and continue business function in case of a cyber attack. This comprehensive plan is designed to give you the peace of mind knowing that your business will continue to function after an attack. Part of the planning includes setting up and testing backup and restore systems. Developing a playbook with step by step plans of what employees should do in case of such an attack.
POLICY & PROCEDURES
We help developing a comprehensive cyber security policy and procedures for your company that will be at the core of keeping your organization protected from the employees themselves. Since most attacks are socially engineered ensuring your company has proper employee policy and procedures in place will help safeguard your systems.
"I am so happy I chose to go with Alphacis to manage our systems and security. I receive weekly reports, and know that my company is truly protected from external threats"
-Trent B. CEO
SCHEDULE A QUICK CALL TO SEE HOW ALPHACIS CAN PROTECT YOUR BUSINESS FROM CYBER THREAT

SPEAK WITH AN IT CONSULTANT. NOT A SALES GUY!
EXPLAIN YOUR BUSINESS TECHNOLOGY NEEDS
RECEIVE AN ESTIMATE WITH PRICING AND OUR SOLUTION BROKEN OUT IN DETAILS
NO PUSHY SALES GUYS OR FOLLOW UP SPAM MAIL
Latest News in Cyber Threats
Industry news, threats and highlights in the tech world.
Atlanta Businesses: The Risk of Malware is on the Rise!
April 19, 2024
Attention Metro Atlanta Businesses: The Risk of Malware is on the Rise! Let's dive into an urgent and crucial topic for today's business landscape: Malware threats. It's not the best news, but it's essential to be informed. Malware attacks are increasingly targeting small and medium-sized businesses (SMBs) in our area, and the consequences can be severe. This means it's more important than ever to understand how to protect your enterprise. So, what is malware? Imagine malware as the digital…
Supercharge Productivity with These Microsoft Edge Hacks
April 14, 2024
Supercharge Your Productivity with These Microsoft Edge Hacks As a busy business owner or manager, you're always on the lookout for ways to streamline your workflow and get more done. While your web browser may seem like just a tool for accessing the internet, Microsoft Edge on Windows 11 is packed with features that can truly supercharge your productivity. Let me share five of my favorite Microsoft Edge tricks that will have you working smarter, not harder. Split Screen for…
These 4 methods will save thousands in case of a data breach
April 16, 2023
These 4 methods will save thousands in case of a data breach! No business wants to experience a data breach - it's like a digital nightmare come to life. Unfortunately, with today's cyber landscape, it's increasingly difficult to avoid them altogether. In fact, according to IBM Security's 2022 Cost of a Data Breach Report, a staggering 83% of organizations have suffered more than one data breach. Data breaches can hurt a business in many ways - from the immediate cost of remediation to lost…
Healthcare & Dental
March 20, 2023
ACIS can manage your complete IT environment from network, endpoint EHR systems and security. We help transition EHR systems and provide security to ensure your practice is HIPAA compliant and your patient data is protected
Dealerships & Automotive
March 20, 2023
Our support for dealerships include working with multiple Dealer Management Software (DMS) vendors, offering fast response times to problems in an industry literarily where time equals money. Our goal is to ensure sales and finance people never miss a beat
Manufacturing & Engineering
March 20, 2023
ACIS has been addressing the technical needs of manufacturing and engineering companies across many different sectors. Our expertise in this field is unrivaled and we have earned a strong reputation as a leader in providing quality support services.
Accounting & CPA
March 20, 2023
We understand the business and cyclical pattern Accounting and CPA firms face such as during tax season and quarterly return times. We make sure to offer 24-7 help desk support to our Accounting/CPA clients during this time
Change this right away in your org: LastPass breach lessons
March 3, 2023
Change this right away in your org: LastPass breach lessons LastPass had a major breach where thousands of accounts had their information exposed Spear phishing was involved Engineer who had encryption keys had his computer compromised Using a keylogger hackers gained access to LastPass AWS servers Below are steps that you can take to prevent this from happening in your business Let's take a lesson from LastPass. If you have not heard yet, there was a major breach last year where encrypted…
These easy steps will secure your mobile devices
February 24, 2023
These easy steps will secure your mobile devices Cybersecurity experts revealed a shocking statistic recently. Malware attacks had amplified by an astonishing 500% during the opening months of 2022. This is particularly concerning considering many people still haven't taken any steps to safeguard their smartphones. For years now, the power of mobile phones has grown exponentially, to the point where they can do many of the same things as a computer. Despite this fact, people have been known to…
Protecting Your Business: Simple Guide to Endpoint Security
January 27, 2023
Summary Companies of all sizes have a variety of endpoints, such as computers, mobile devices and servers. Endpoint security is necessary to protect against malicious attacks from hackers. 64% of organizations have experienced one or more compromising endpoint attacks. Solutions for addressing password vulnerabilities include training employees, MFA and biometrics Stop malware infection before OS boot Regularly update endpoint security software and firmware Use modern device…
Easy cybersecurity guide: increase security, lower overhead
January 20, 2023
Answering these cybersecurity questions correctly will lower your insurance rate and make your business more secure Do you have a formal Cybersec policy for all employees and is it enforced? Is multifactor authentication enforced companywide? Do you have a formal Disaster Recovery Plan? Who has elevated permission or Administrator access to the system? How are passwords safeguarded? Are you running a company-wide advanced threat detection and protection, and can you prove…
Easy way you can prep your business technology (IT) for 2023
January 4, 2023
Easy way you can prep your business technology (IT) for 2023

This process will protect your business from ex-employees
December 9, 2022
This process will protect your business from ex-employees Every employee in the modern workplace creates a digital footprint. This starts as soon as they're hired, with a company email address and application logins. They may even update their LinkedIn page to show their connection to your company. When an employee leaves a company, it's important to go through a process of, "decoupling" them from the company's technology assets. This digital offboarding is vital to cybersecurity. To avoid…
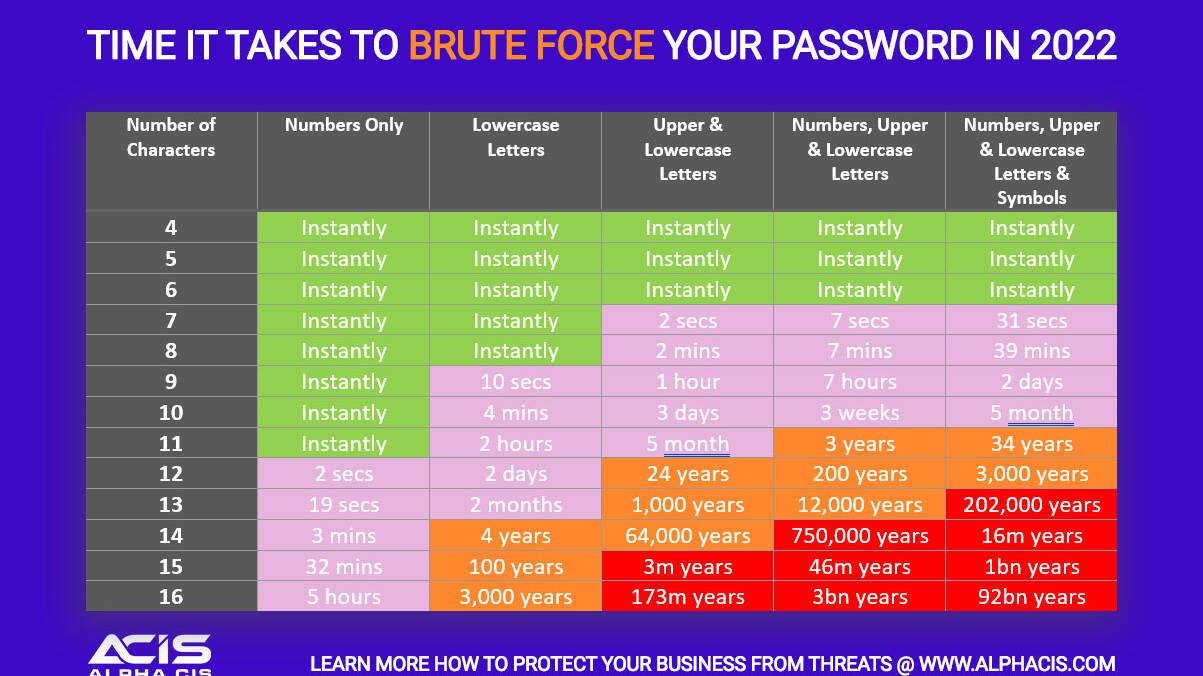
Easy tricks anyone can use to memorize complex passwords
November 22, 2022
Easy tricks anyone can use to memorize complex passwords Why you shouldn't follow the minimum password strength requirements! A password is normally one, (and sometimes the only wall), preventing an attacker from gaining access to your systems or data. Most of what are considered strong passwords require: 8 characters One Capital One Lower Case Number Symbol Here is an interesting fact, a password of this complexity can be cracked in 48 minutes, using a couple of the latest graphic cards.…
5 Mistakes Companies are Making in the Digital Workplace
October 20, 2022
5 Mistakes Companies are Making in the Digital Workplace Employees are increasingly working remotely, and as a result, companies are struggling to keep up with the changing landscape of the digital workplace. From unauthorized app use to remote work-related stress, we will discuss 5 mistakes companies are making in the digital workplace. The pandemic has forced companies worldwide to change the way they operate. No longer can everyone work in the office like before; many organizations had to…
6 easy IT policies all companies should implement right away
September 21, 2022
6 easy IT policies all companies should implement right away! Many small businesses make the mistake of skipping over policies. They believe that formalities are not necessary. They will simply inform staff what is expected when it comes up, believing this to be sufficient. However, this attitude might lead to problems for small and mid-sized business owners. Employees are not mind readers; they may misinterpret your intentions. If you don't have any rules in place, you risk being in a bad…
6 Technologies You Shouldn’t Use Anymore. Checkout #5!!
September 19, 2022
6 Technologies You Shouldn't Use Anymore. The pace at which technology develops is unquestionably rapid. Tools that were once must-haves, such as Internet Explorer and Adobe Flash, become antiquated. New tools take the place of old ones. Vulnerabilities in outdated technology can leave computers and networks open to breaches and malware infections. While older technology may still operate properly on your systems, this does not imply it is safe to use. Software and hardware that are no longer…
Employee Left- How to secure Wi-Fi from previous employee
August 15, 2022
Employee Left- How to secure Wi-Fi from previous employee Did you know that if someone has the password, they have complete access to your network? In general, I see that these passwords seldom change. Employees come and go, but the Wi-Fi password at most businesses is solid and unchanging for many years. Generally speaking, the way 99% of the networks are setup are as follows: You have your LAN - (physical network of firewall and switches) Internal Wi-Fi - A network that extends the physical…
This free Microsoft tool massively increased my productivity
July 20, 2022
This free Microsoft tool massively increased my productivity
If you are like me, you probably ditched your 2 monitor setup for an ultra wide, or perhaps 2 ultrawide. If you did jump on this trend then you quickly realized that you have a lot more real-estate to manage and organize when working with multiple windows on our computer. With ultrawide screen monitor, you probably already know that lining up 3 windows next to each other can be a task that takes time from your productivity.
Get any old unsupported printer to work with Windows 11
July 9, 2022
Get any old unsupported printer to work with Windows 11 We have all been there, when you have to get rid of your good printer because it's no longer supported by the new version of Windows. Now, this is frustrating if it’s a home printer that can be replaced for a few hundred bucks, but what if it’s a large printer that is worth $5,000 that is no longer supported. This is something that a lot of businesses are struggling with, as they don't want to spend the money on a new printer when their…
How to get your Managed IT Services for free
June 16, 2022
How to get your Managed IT Services for free There's no doubt that running a business is expensive. From the cost of goods and services, to the price of office space and employee salaries, there are a lot of expenses associated with keeping a company up and running. Bills, such as cable, internet, and telephones can sometimes add hundreds, if not thousands of dollars, depending on the location to your bottom line. One of our client’s has been using a traditional bonded T1 service through…
Who needs managed IT services(MSP)? Not this guy…
June 2, 2022
Who needs managed services? Not this guy... "Why do I need to pay for an MSP? It's not like my computer breaks often..." Typically, what I hear from clients, is that they that look at an MSP as just another utility bill, like your phone or internet. It's really much more than just another overhead expense. A good MSP relieves you, your management, and your staff, from the technical aspect of your business. It allows everyone to focus on their jobs, knowing that supporting technology will work…
How to quickly setup your office network the correct way
May 11, 2022
How to quickly setup your office network the correct way .player101781 .plyr__controls, .player101781 .StampAudioPlayerSkin{ border-radius: px; overflow: hidden; } .player101781{ margin: 0 auto; } .player101781 .plyr__controls .plyr__controls { border-radius: none; overflow: visible; } .skin_default .player101781 .plyr__controls { overflow: visible; } Your browser does not support the audio element.…
How to quickly secure your network from rogue IoT devices
May 6, 2022
The easy way to secure you IoT devices and systems .player101783 .plyr__controls, .player101783 .StampAudioPlayerSkin{ border-radius: px; overflow: hidden; } .player101783{ margin: 0 auto; } .player101783 .plyr__controls .plyr__controls { border-radius: none; overflow: visible; } .skin_default .player101783 .plyr__controls { overflow: visible; } Your browser does not support the audio element.…
Separate duties for employees or end up like this…
April 21, 2022
Separate duties for employees or end up like this... With war in Ukraine raging on, the cyber warfare between the Russians and the West continues to see an increase in Russian cybercrime. We deal with a lot of clients that employ external developers for specific projects. What we frequently discover is that these external developers and internal operations have little separations of responsibility. For example: Here is an illustration of something we just experienced with a customer. They are…
10 Ways you can fight against Russia’s cyberattacks
April 12, 2022
10 Ways you can fight against Russia's cyberattacks I had the pleasure of attending the Tech Execs Summit in Forsyth. They brought several speakers that had a lot of insight into how and why Russia's cyberwar is impacting local businesses. We are no longer threatened by the one man show that just got lucky and was able to hack into your system and get $500 in ransom out of you. These hacking organizations are ran as a business in Russia, as in they have office space, they have employees, they…
5 things: When selecting best IT Services Co. in Alpharetta
March 28, 2022
5 things: When selecting best IT Services Co. in Alpharetta This post will discuss the factors to consider while selecting an MSP for your business. Choosing an MSP is a big step in deciding to outsource or enhance your IT needs, and there are many things to think about when it comes to how it fits with your company's goals. Let's assume you're a firm of 20 employees in Alpharetta, Georgia. You previously utilized an "IT Person," to take care of day to day fixes here and there, but as your…
Data breach the new extortion method: backups are not enough
March 12, 2022
Data breach the new extortion method: backups are not enough

What to do NOW as war in Ukraine increases cybercrime
March 8, 2022
What to do NOW as war in Ukraine increases cybercrime As the war in Ukraine keeps escalating, many more cyber-crime groups are starting to emerge as a result. Why do you think this is happening? In places around the world that don’t have many opportunities to make money legitimately turn to crime to provide for their families Now let's fast forward to what is happening in Russia. Crippling sanctions have devalued the Rubel, and many vendors, companies, and industries are turning their backs on…
Top 3 cybersecurity trends to prepare for in 2022
February 21, 2022
With the COVID pandemic mostly behind us, we are faced with the reality that the workplace has forever been changed. Security is on the top minds of most business owners and CIO’s out there. Here are the new trends that we will see more of in the coming year. Location Independent Security is no longer relying on a centralized firewall Let’s rewind back to 2019, every employee comes into the office, they login to their desktop computer that was assigned to them, they work until 5pm, then, they…
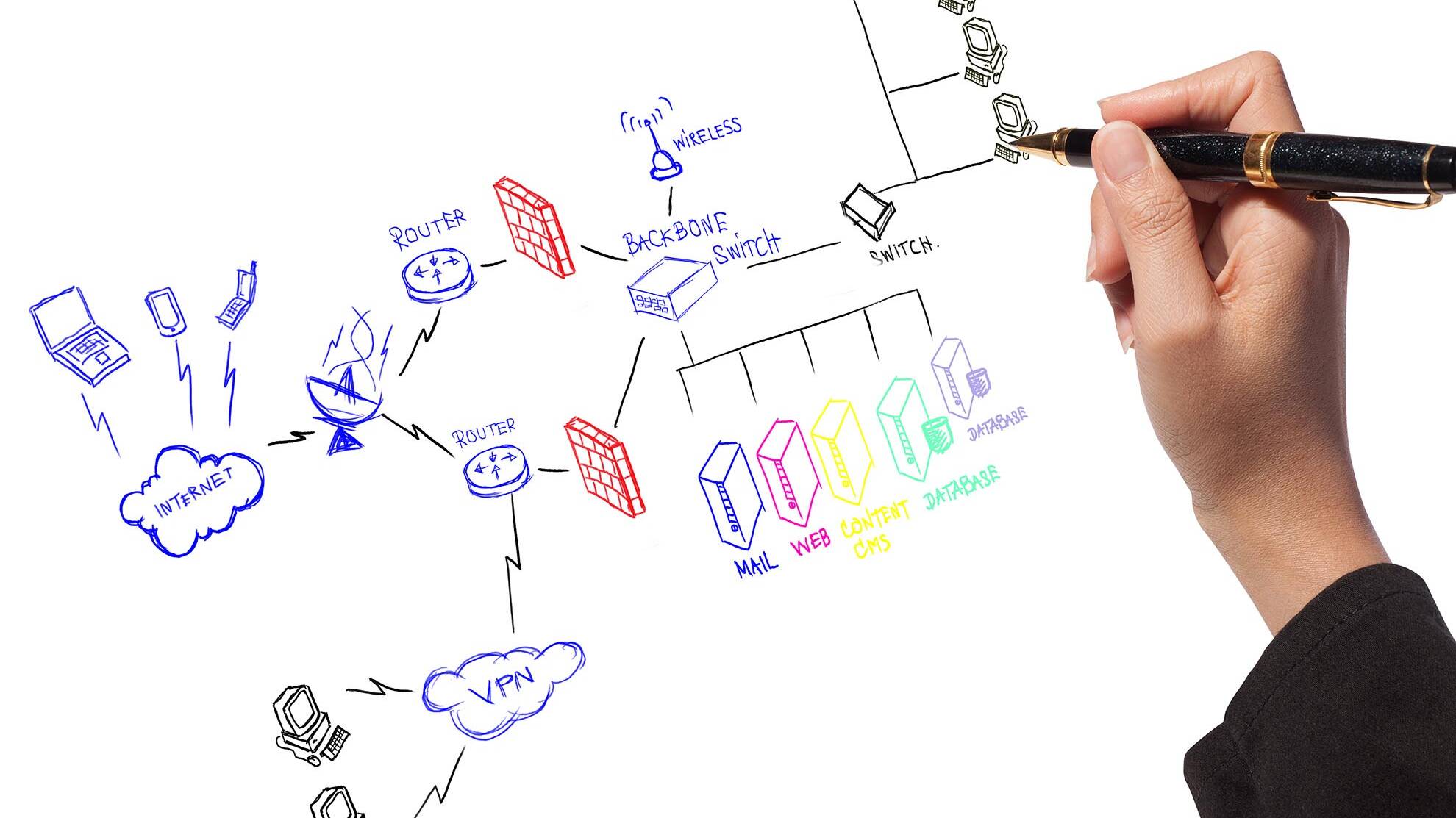
What makes a good network map, and why you should care
February 17, 2022
What makes a good network map, and why you should care Do you have a network map? Chances are that if you work in networking, you do. Or did you know what a network map was before reading this article? The term is used very often and hardly anyone knows what it means. This article is intended to give an explanation of what a network map is, and why you should have one. First of all, what is a network map? A network map is a visual representation of your current and planned topology – the layout…
What John did to lose his data storing it in the wrong place
February 13, 2022
What John did to lose his data storing it in the wrong place I’ve worked with many clients in different industries; however, what I noticed is always common in majority of the businesses that we take on as clients is the lack of uniformity and processes. This includes how data is stored, handled, and transmitted. The lack of standardization creates a huge problem when it comes to keeping up with backups, ensuring there is even a backup, and also causes problems when training new employees on…
Before & after the cybersecurity training
February 7, 2022
Before & after the cybersecurity training Let's pose a scenario: Your top client receives an email from you that sounds awfully suspicious, it may go like, "Hey, I sent you the document you requested. Click this link to download the PDF." If your clients are smart, they would quickly reply to you if they think something is strange about the email. They would want to confirm if you actually sent the email. Imagine what would happen if your mailbox was either spoofed or compromised. Attackers…
3 steps to safeguard your Network Attached Storage (NAS)
February 2, 2022
Network Attached Storage (NAS) devices can be great resources on your network when it comes to centralized storage accessible to all devices on the network. The issue is that this centralized entity may be accessed from outside the network.
This past week, QNAP NAS devices have been targeted by a .deadbolt ransomware. Owners will wake up to find their data has been locked with a .deadbolt extension and ransom demands of $1,100 in bitcoin are being made so that they may unlock their data.
Security settings to change right away on your Macs
January 28, 2022
Security settings to change right away on your Macs Apple users are still just at risk of phishing attacks as any other user on any device. Although Macs come with XProtest and Gatekeeper designed to keep users safe, socially engineered attacks still don't prevent end users from handing over their credentials. If you are using your Mac for work, here are some of the things I recommend users to do on their Mac computers right away. Best practice Mac security settings to implement right away…
Quick Disaster Recovery plan to implement now for 2022
January 24, 2022
Quick Disaster Recovery plan to implement now for 2022 You have heard the words Business Continuity and Disaster Recovery being thrown around; however, I know a fiery earthquake or the great flood might not be the top of your concern. Sadly, a disaster in today's world comes in the form of cybercrime. According to TMC.net, 50% of companies that experience a cyber attack go out of business within 6 months of the attack. This is not surprising when you consider the number of preventable data…
How hackers are getting around Microsoft Defender
January 18, 2022
How hackers are getting around Microsoft Defender Microsoft presents Windows Defender as a one-solution fits all, however as we learned that is certainly not the case in the cybersecurity world. Cybersecurity should be tailored towards a particular business, there is rarely one size fits all approach here. Microsoft Defender lets users add locations or network locations to the list of excluded areas to be scanned for malware/viruses. Users commonly add folders and paths to Microsoft Defender in…
How to sell Cybersecurity by partnering instead of selling
January 11, 2022
How to sell Cybersecurity by partnering instead of selling Here is the deal, the threat actors don't care for the size of the business you have. An example can be, a small software development company that does work for larger firms. Having their clients’ data leaked can be detrimental to them. They might not have millions to pay in ransom, but the threat actors don't really care. They are perfectly fine collecting $5,000 from you and 1000’s of others. So, when I speak with a client about their…
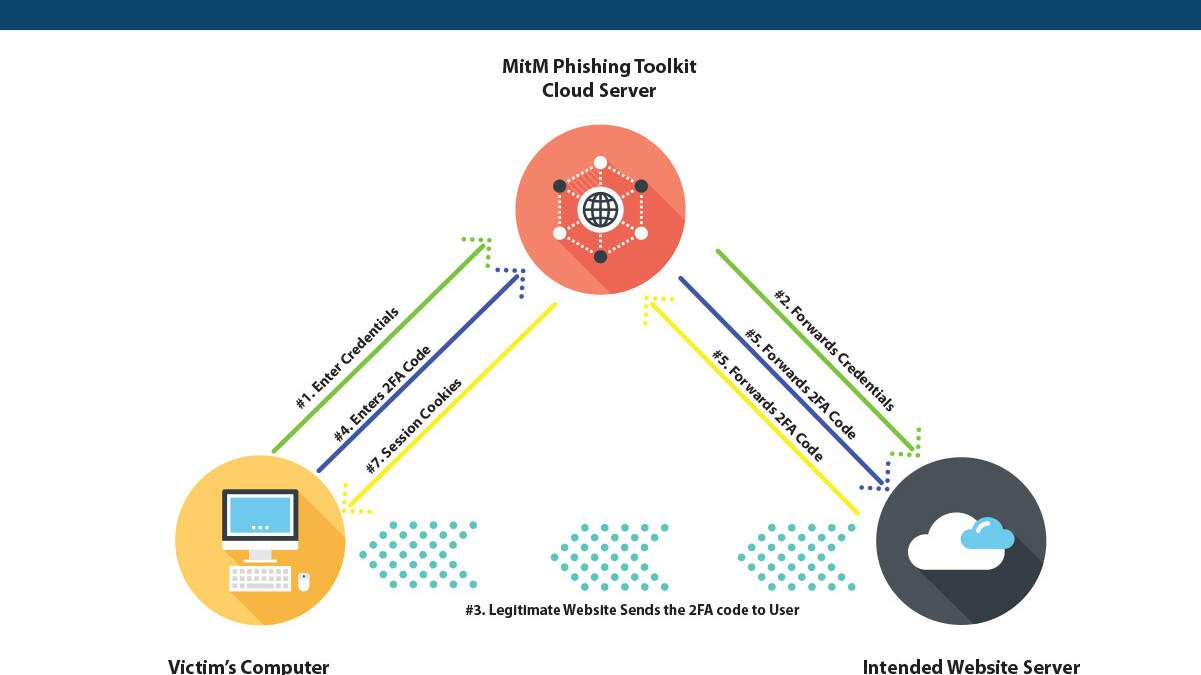
Are you sending your credentials to a MitM without knowing it?
December 30, 2021
Are you sending your credentials to MitM without knowing it? About a month ago, we reported that some phishing kits had added the capability of intercepting SMS-based 2FA tokens. Since then, we decided to look for more such tools and found a whopping 1200+ web-based phishing kits in our research, which are capable of intercepting 2FA when it is used by unsuspecting users. These toolkits enable any wimpy "hacker" to utilize the MitM (Man-in-the-Middle) attacks. After many major tech companies…
Security settings you need to change right away for 2022
December 27, 2021
Security settings you need to change right away for 2022 Often times we think of security solutions as just an antivirus and you are done. At least that's what most business owners assume it takes to secure their systems. But outside of only installing and running an antivirus solution there are policy that windows by default allows. Depending on the environment, I like to make sure that our client's systems are as secure as they can be without breaking their software and work flow. Sometimes…
Why you should care about the Log4J vulnerability
December 21, 2021
Why you should care about the Log4J vulnerability Apache is an HTTP server that is open-source, cross platform and represents about 33% of all websites on the internet and countless applications that utilize parts of it. Log4J is a Java logging library used by the Apache server and many of those applications. A vulnerability was recently discovered in Log4J that could allow an attacker to execute malicious code on the target system. The vulnerability specifically affects versions 2.x and 3.x of…
How to quickly pass a PCI compliance scan
December 17, 2021
How to quickly pass a PCI compliance scan The Payment Card Industry Data Security Standard (PCI DSS) is a set of regulations that businesses need to follow in order to protect sensitive credit card and personal information. It can be hard for small business owners who don't know how the PCI DSS works, but there are some steps you can take to get compliant quickly and easily. In this blog post, we will discuss what it takes to become compliant with the standards and why you should care about…
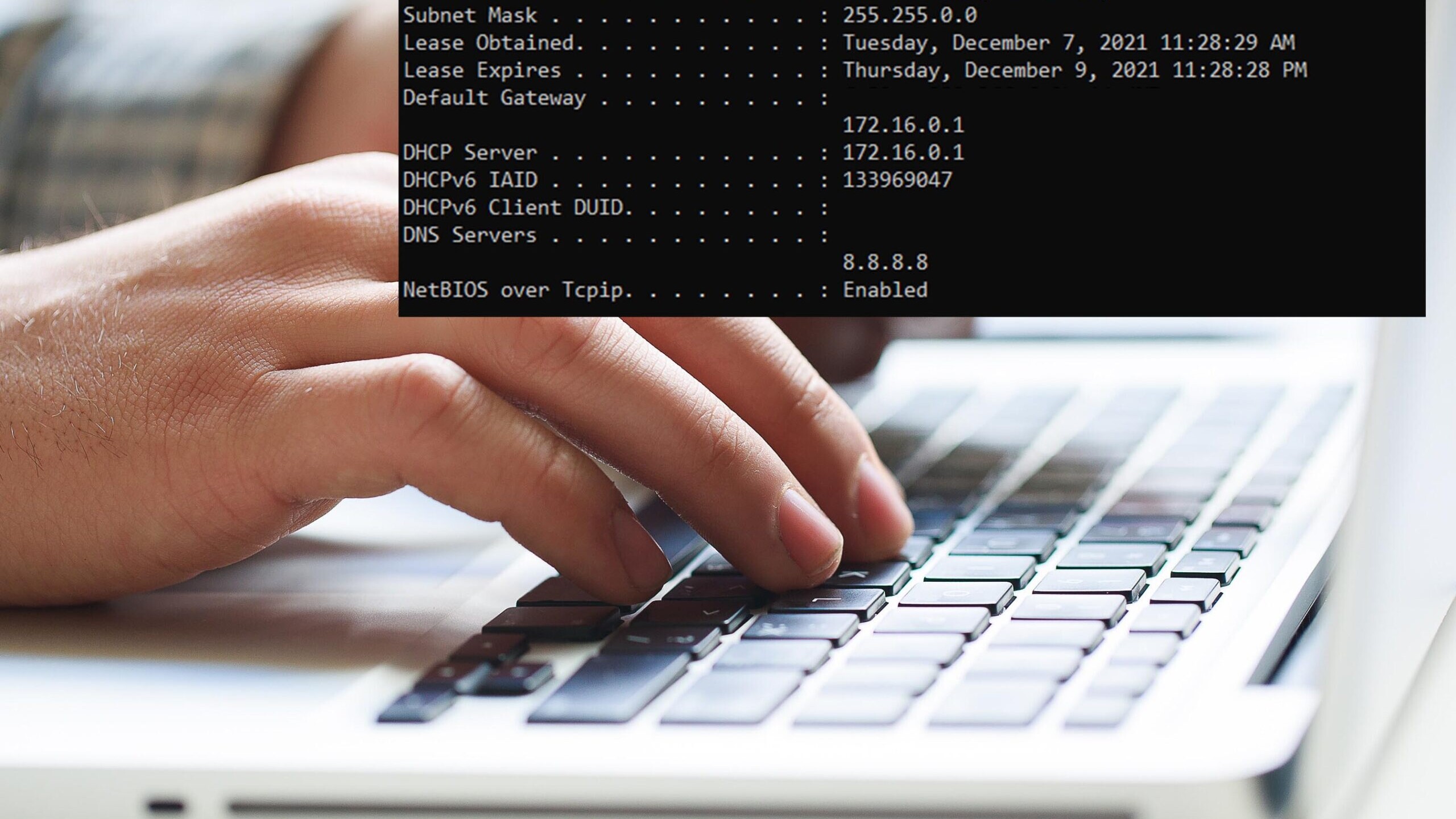
Tricks to diagnose and restore your internet connection
December 10, 2021
Tricks to diagnose internet connection from your seat I ask this question on interviews when checking to see if a technician knows basic networking, and you would be surprised how many do not! I will help you out without getting technical, explaining how packets are sent, and how IP addresses work. This is a tutorial with real life situations and a step by step process you can take to solve it. So, you come into the office and you are greeted with the following error stating there is no…
James received a message, “what’s this link you sent me??”
December 7, 2021
James received a message, "What's this link you sent me??" James received a reply back from his co-worker telling him that he sent them a drobox link that looked suspicious. The next day another person complained to James telling him he sent them a google doc that is asking to login and they just wanted to clarify what it was. James quickly realized someone got a hold of his company email password and has been sending spam out of his mailbox. He quickly did what he thought was the most…
These 2 simple things could save your business from a cyberattack
December 6, 2021
These 2 simple things could save your business from a cyberattack It's interesting when I hear from CEO's and business owners the usual "We are not big enough to get hacked," or "Why would anyone want to target us?" What I always tell our clients is that the threat actors don't care what you do, they don't care how much money you make, all they care about is that you make it, all they care about is that you have an open system, or you fell prey to a phishing, or spear phishing attack, and they…
MSP tips for SMB – Enterprise backup on budget for your organization
November 29, 2021
MSP tips for SMB - Enterprise backup on budget for your organization Some may think when selecting a Managed Services Provider MSP, that we have access to some magic secrete sauce programs, or develop things in house to help secure or backup or manage your systems. We use the same software available to most business owners! Keep in mind I am in no way shape or form getting paid by any of these companies or services that I talk about below, so I just want to make it clear that this is strictly…
How do you migrate to Office 365? Smoothly…
November 26, 2021
How do you migrate to Office 365? Smoothly... If you are on a different hosted platform of exchange, it takes careful planning, staging, and execution and communication with end users. Understanding the environment and gathering as much information as possible is the first critical step. This ensures no surprises happen later or you come to a step where you aren't sure how to proceed. We must first answer some questions prior to migration Are we only moving email boxes or other office…
Still not on Office 365? Here is a good reason to switch…
November 23, 2021
Still not on Office 365? Here is a good reason to switch... Reasons why you should migrate to Office 365 if you are still on another platform. By now I don’t have to explain the benefits of exchange email and why its much better than SMTP and POP3. What is Exchange or Office 365 email? Let's just put it this way, if you want a centralized location for your emails that you are accessing with multiple devices, your cell phone, computer, tablet etc. All emails read on any device will be kept and…
8 things to do in case your systems have been breached
November 19, 2021
8 things to do in case your systems have been breached Finding out that your company has been the latest unwitting victim of a ransomware attack capable of restricting computer systems and encrypting data if a ransom is not paid to cybercriminals would be a nightmare for many corporations. There is no such thing as a magic wand that can make a ransomware assault disappear without some down time, sweating, and getting your IT team involved in restoring systems. 1. Do Not open the ransom…
Quickly check the Dark Web for your leaked credentials… without checking the Dark Web
November 16, 2021
Quickly check the Dark Web for your leaked credentials… without checking the Dark Web Ever wonder if your most used username and password is floating out there in the dark web, but don't want to install a Tor browser, start visiting questionable underground websites, downloading data dumps by hacking groups and spending hours running queries to find your username and password present in these databases? You are in luck because Google did all the hard legwork for you. Chrome is a…
So you think 2FA is protecting you… That’s cute
November 8, 2021
So you think 2FA is protecting you... That's cute The phone rings, a voice on the other end states, "Welcome to Chase Fraud protection department, we have recently receive a charge from E Constants online retailer for $74.32. If this was not you, please press 1." A few seconds later the phone buzzes and it's a text message from 227895 number which is the same number you always receive the verification code from. You quickly type it in to confirm that it is in fact you. The voice continues:…
What your “IT Guy” won’t tell you. MIGHT hurt you…
November 3, 2021
What your “IT Guy” won’t tell you. MIGHT hurt you… I'm sure there's more than one IT person who's reading this wondering what they've done to be scrutinized. But here it goes.... Things that are common with "IT Guys" I will first list out some of the concerns that you should think about, and then we can dive deeper into them… Single Point of Failure Poor Documentation Security Risk Can't be the” Jack of all Trades” Single Point of Failure I can't stress enough how important this point…
If you have Office 365, you should utilize Azure AD to protect your firm for free!
November 2, 2021
If you have Office 365, you should utilize Azure AD to protect your firm Office 365 is Microsoft's cloud productivity suite, with comparable features to Google's G Suite. It includes online versions from many of the most-used Office applications, including Word, Excel, and PowerPoint. A basic version of Azure AD is included FREE of charge with your Office 365 subscription! One compelling feature of Office 365, that your firm may not know about, is Azure Active Directory (Azure AD),…
The biggest cybersecurity threat in 2021 and 2022 affecting all businesses
November 1, 2021
What is the biggest cybersecurity threat to businesses in 2021 and 2022 that affects all businesses The types of cyber attacks that pose the most serious threat vary depending on the business. There are many different kinds of attacks that hackers might launch, including phishing attempts, ransomware, distributed denial-of-service (DDoS), and more. However, not all threats are created equal. For example, a ransomware attack is usually much more harmful than a DDoS attack because ransomware…
What is the cost for managed IT services in Atlanta?
October 28, 2021
What is the cost for managed IT services in Atlanta? What is the cost for managed IT services in Atlanta in 2023? The answer to this question varies depending on the companies and services they offer. Most MSPs will sound the same when it comes to the service and their promises however; every offering is different and you will be hard pressed to find two MSPs that use the same tools in their offerings stack. An offerings stack is basically the technology your MSP uses to deliver their…
What 5 minutes of interruption can do to your workflow
October 21, 2021
What 5 Minutes of Interruption Can Do To Your Workflow I think it’s safe to say that everyone agrees, time is money. Interruption in our tasks can add up very quickly. For example, a study done at The University of California by Gloria Mark, says that it takes about 25 minutes to return to the original task after an interruption. There are multiple studies that also confirm, distractions don't just eat up time during the distraction, they completely derail any sort of productivity for almost 30…
How Invisible IT Costs Add up fast & How to Calculate Them
October 20, 2021
How invisible IT costs add up quickly and how to calculate them When you hear Managed Service Providers (MSP) companies talk about saving you money, making things more efficient etc., etc., (insert more IT jargon here). What does this all mean? Hiring an IT support provider costs companies money right? So how do they claim to solve world problems and save your business money? Let's start by defining what an MSP is, the promises that MSPs make, how they plan to save you money, and how to tell…
How Lisa had her paycheck stolen – Phishing Attack
October 14, 2021
How Lisa had her paycheck stolen - Phishing Attack Here is how Lisa had her paycheck stolen. Lets walk through the events leading up to it and how it actually happened! BECKY FROM HR Received an email from an employee named Lisa requesting to change her paycheck to be deposited into a different bank account. Becky sent a reply with an attached document labeled “ACH Bank Change Form” to change the bank where the money is going to be transferred into this Friday for payroll. She received an email…
Retrofit your computer with biometric for $80
October 8, 2021
In the spirit of October Security month. We have used biometrics to unlock our phones, pay at the grocery stores, log in to our bank accounts for many years now. It only makes sense that this level of security makes it into mainstream day-to-day use on our desktops and laptops. Although many devices already include this feature such as a fingerprint reader, Yubicon now offers a retrofit for older devices to utilize biometrics instead of passwords. Check out this $80 USB key that doubles as a…
What it was like for a CPA firm to survive a cyberattack
October 5, 2021
What it was like for a CPA firm to survive a cyberattack I met Joe at a networking event, he is a CPA and owns his own Public Accounting Firm. Over time we became friends and I assisted his MSP (Managed Services Provider) on several IT projects. He employs 12-15 accountants depending on the time of the year. One Friday, Joe noticed that his systems were running a little slow. Being that it was a Friday afternoon, and having had dinner plans in a few hours with his family and a few friends, he…
Skip the line! Install Windows 11 and don’t wait for automatic update!
October 5, 2021
Outside of a controversial Start Menu, windows 11 appears to be mostly familiar to everyone. You can checkout the new features from Microsoft. However if you don't want to wait until the new update arrives to your computer as an automatic update. Don't worry, just head over to Microsoft and download the new update. This link will take you straight to MS page where you can download the update for FREE! You can create installation media like a USB drive or create an ISO. Really easy. If you are…
Network closet cleanup. How to save money & organize data closet
September 30, 2021
Network closet cleanup. How to save money & organize data closet If your data closets look like a rats nest with unorganized unlabeled wires everywhere, congrats, you are in with the majority! Most of our clients that we come across have a similar issue. Its easy for multiple vendors, your staff and everyone else having their hand in the network closet. No one really wants to fix it since its viewed as an unnecessary and expensive endeavor to…
Microsoft Explains why Windows 11 will be soo much faster!
September 15, 2021
This 12 min video explains all the features of upcoming Windows 11 and what will make it soo much faster than windows 10. Its pretty impressive that microsoft listened to the feedback of the beta tester program and made the suggested improvements. The real interesting feature is how you will no longer put your computer to sleep / power it down. It will work similar to what your phone does when it is not touched for a few min. The screen will turn off and the only thing that will remain powered…
Stop ransomware with these TWO steps
September 15, 2021
Stop ransomware with these TWO steps In a world where you can sign up as Ransomware As A Service its no surprise that its soo profitable and soo lucrative that everyone must take the steps to ensure they are protected, because everyone is a target. Windows 10 and 11 comes with many security features that you might not know about that can help in protecting your systems. Although 3rd party AntiVirus solution is advisable, taking these simple TWO steps can further increase the security of your…
500,000 Fortinet VPN Credentials Just Got Leaked
September 10, 2021
500,000 Fortinet VPN Credentials Got Leaked on Hackers Forum The list of Fortinet VPN credentials was released by a malicious actor known as "Orange," who is the administrator of the recently launched RAMP hacking forum and a past leader of the Babuk Ransomware initiative. Almost 500,000 Fortinet VPN login names and passwords that were scraped in an exploit on multiple devices a year ago. Orange split off to form RAMP and is now thought to be a representative of the new Groove ransomware…
Read this before you hire an IT support company…
August 18, 2021
CLICK PLAY TO LISTEN TO THIS ARTICLE [audio src="https://www.alphacis.com/wp-content/uploads/2021/08/Murf-7.mp3" /] When your business needs to move beyond what you can DIY on your own, it might be time to start thinking about outsourcing your IT. Every company has a different set of needs and various levels of expertise that is needed. You should evaluate which outsourcing service is best for your organization to minimize risk and overhead. This article will talk about the things to consider when evaluating…
Remove NAS from Active Directory (AD) Right Away!
August 6, 2021
If you are able to connect to your Network Attached Storage Device with your Active Directory credentials it might be a good idea to change the way your NAS authenticates. Ransomware attacks on the rise its hard to think of a work environment where inside the network should be thought of as unsecure space. Unfortunately with social engineered attacks, such as phishing and new exploits being found daily it’s the reality in 2021. Once the hackers gain access to the network, they can encrypt local…
Do This Now to Reduce Cyber Insurance Policy Costs
July 21, 2021
When it comes to insurance reducing exposures is what underwriters generally focus on to determine the premium costs: Are you storing sensitive data? Are you running credit cards through your terminals? Is your staff trained in security? Do you run backup software and do you test these backups periodically? Are you using firewalls and AV software and is it up to date and managed? Do you have a 3rd party company or internal employees that specialize in managed your network and security?……
Why Your Business Will Need Next Generation Firewall (NGFW)
July 10, 2021
What is a next-generation firewall (NGFW)? A next-generation firewall (NGFW) is a network security appliance capable of inspecting traffic at the protocol level. An NGFW can enable companies to block unauthorized access, prevent malware from entering the network and securely accelerate business applications. This takes things one step further with not just inspecting packets going in and out of the network, but breaks things down further depending on the applications. What is the difference…
ALL CPA firms should register .CPA Domain while it’s still available!
July 5, 2021
AICPA launched a new CPA-specific top level domain (TLD) that will help you build trust and reach your clients in a more secure way. This verification process ensures that only those who meet certain requirements can register for this TLD, which adds another safeguard and level of trust for potential clients. If your practice hasn't jumped on getting their .CPA domain yet I suggest you do this right away. Unlike .com .net .org or many others that anyone can register for, .CPA MUST in fact be a…
Cybercriminals Are Now Targeting CPA and Accounting Firms 🔐
June 29, 2021
Cybercriminals Are Now Targeting CPA and Accounting Firms Reasons for targeting accounting firms is almost obvious. Consider if you are trying to get sensitive information such as bank accounts, access to retirement and investment accounts, social security and EIN numbers. What industry would you turn to as a hacker ? The answer is clear, ✅ CPA and accounting firms. Unfortunately, too many of these firms have much of this sensitive client information sitting on a network drive or local…
5 Ways Dealerships Can Save Money On I.T. Costs
June 16, 2021
1. Stick with one vendor for managing I.T. Think of services with a major cable company or Internet provider. It’s always cheaper when you bundle multiple services, like internet and T.V., and/or phone. This concept is also true when it comes to selecting an I.T. services vendor. Much like a Dr., you would not want a brain surgeon operating on your heart. This is also true when it comes to IT providers as well. An I.T. company that dabbles in 20 different industries more than likely…
Do these 3 things right now to prevent ransomware on your systems!
June 9, 2021
Do these 3 things right now to prevent ransomware on your systems! Quick and simple, ransomware works by encrypting your hard drive and any device connected to your computers. This makes all of your files inaccessible and you will see text documents in every folder with instructions on how to pay the ransom to get your files decrypted. A fun fact about ransomware is that in 2020 the attacks increased by 130%. If you break down that number, 81% of the total infected are enterprises, and 62% of…
Fire your IT guy if they do any of these things…
June 7, 2021
Why you should fire your IT guy Over time things change, people change, and your organization's needs change as well. Here are some of the things to look out for with your current IT guy. Complacency Number one reason to fire your IT guy is complacency. Just like politicians holding the same public office position for 20+ years, they get use to the easy life! Doing things “the way they have always been done” is one of the easiest ways to spot complacency! “The way things have been…